ELLIPAL Blog
ELLIPAL Celebrates Six Years: The Originator of...
In March 2024, ELLIPAL, renowned as the pioneer of air-gapped cold wallet technology, commemorates its sixth anniversary. Instead of a subdued acknowledgment, they're igniting a month-long airdrop celebration, broadcasting their...
ELLIPAL Celebrates Six Years: The Originator of...
In March 2024, ELLIPAL, renowned as the pioneer of air-gapped cold wallet technology, commemorates its sixth anniversary. Instead of a subdued acknowledgment, they're igniting a month-long airdrop celebration, broadcasting their...
The Dangers of Physical Attacks on Your Hardwar...
Not long ago, another well know hardware wallet got hacked under test conditions, and it wasn’t the first one this year either. Among all these hacks on the famous hardware...
The Dangers of Physical Attacks on Your Hardwar...
Not long ago, another well know hardware wallet got hacked under test conditions, and it wasn’t the first one this year either. Among all these hacks on the famous hardware...
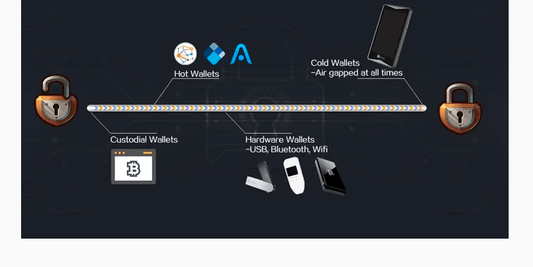
ELLIPAL- The Best Security from Air Gapped Hard...
With the rapid and ever-growing evolution of the crypto market along with the introduction on new coins and tokens, users are looking for a more advanced and more secure hardware...
ELLIPAL- The Best Security from Air Gapped Hard...
With the rapid and ever-growing evolution of the crypto market along with the introduction on new coins and tokens, users are looking for a more advanced and more secure hardware...
