ELLIPAL Follows BIP44
Almost every wallet uses what is called as BIP as a system to create cryptocurrency accounts, addresses and allow coins to be transferred. BIP helps create the seed and the mnemonics and allows users to recover their coins in other any wallet that uses the same BIP.
There are a few common BIP types: 32 / 39 / 44, each with different advantages. ELLIPAL choses to use BIP 44 which allows multi-account ability, meaning users can create many accounts all from a single device. This gives users more privacy and ways to manage their coins.
As for your understanding, ELLIPAL follows the standard patch: m / 44' / coin_type' / 0' / 0 / 0
This link shows the registered coins type under BIP 44: (https://github.com/satoshilabs/slips/blob/master/slip-0044.md)
ELLIPAL Follows XRP Official Wallet for XRP
XRP is special because the account can be generated either from BIP44 private keys or from XRP secret keys and these two are not compatible to each other. An example of a wallet that uses XRP secret key is the XUMM mobile wallet or the Ripplefox PC wallet which is opensource and follows the original XRP official wallet.
ELLIPAL also generates XRP accounts from XRP secret keys. If you wish to recover your XRP on other wallets, you will need to find your XRP secret key.
Your XRP secret key can be extracted from the mnemonics of your ELLIPAL account. To extract, download the open source, offline conversion tool available here:
(https://github.com/ELLIPAL/EllipalXrpAddress)
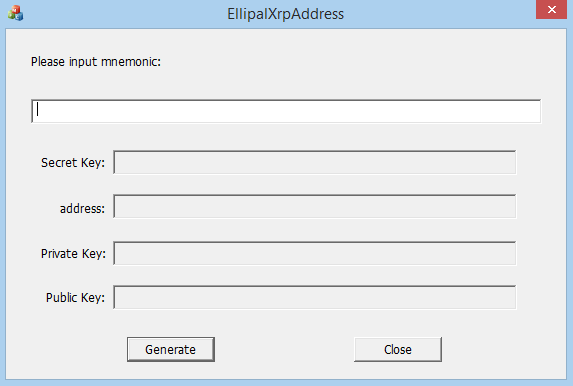
Download the exe. file and install it on your computer (Windows only), input your mnemonics into the program and extract your secret key. You can also use it in offline mode to improve security and protect your mnemonics.
Download EXE file:
Input Your ELLIPAL Mnemonics:

1 comment
Cool, I think more people dont know why XRP is different